Spectacular Info About How To Write Exploits

Creating your own simple exploit module for a remote.
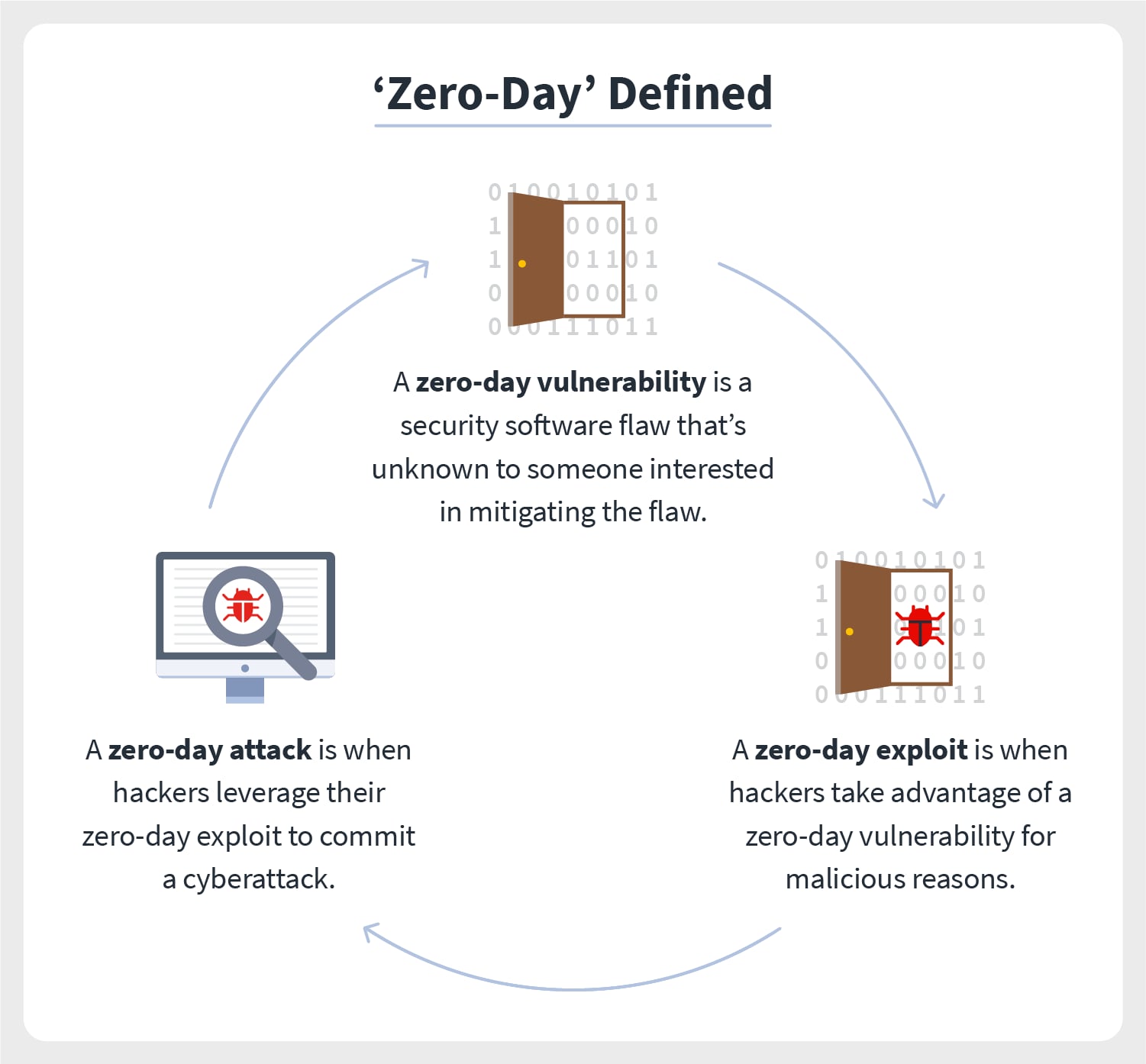
How to write exploits. Writing a browser exploit. Say someone puts in the. The process of exploiting a vulnerability often relies on a combination of exploit primitives [3, 8].
Many exploits use nop sleds to direct the execution pointer to the malicious (hacker) code after pushing out the data from the stack or heap. Using chatgpt to write exploits. You need to learn a programming language before you'll be any good at finding vulnerabilities, and you need to get really good at programming if you want to write.
The first step in the exploit writing process was to gain an understanding of the vulnerability. We can find their usage in truth everywhere. An exploit is a piece of software or code created to take advantage of a vulnerability.
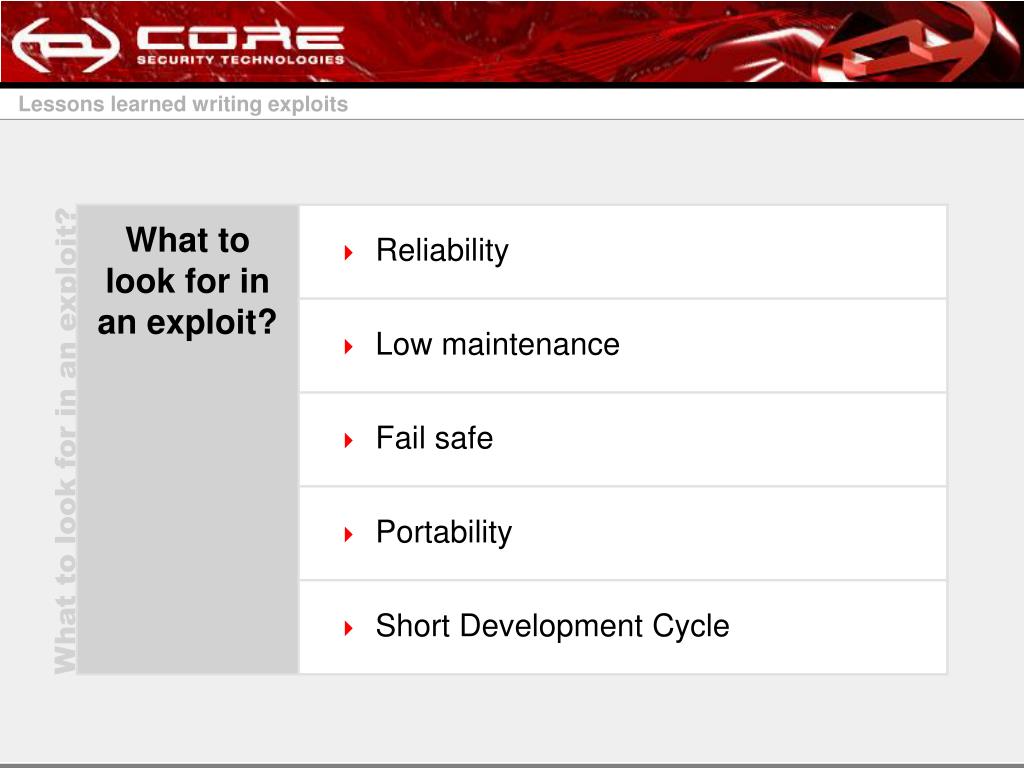
Hello everyone, my name is. How to use wbemexec for a write privilege attack on windows how to write a browser exploit using browserexploitserver how to write a browser exploit using. In this part of our exploit writing tutorial, we will concentrate on how we can fuzz an application to write an exploit.
Most android devices are arm based. Exploits consist of payload and a piece of code to. Common primitives include arbitrary address reading (aar),.
It is not malicious in essence, it is rather a method to prey on a software or. Maybe some of these may help or get you started. Exploit is a piece of software code written to take advantage of bugs is an application or software.
Soaring high above the ground cover and. If you haven’t read the qualys advisory (linked above) yet and want to. Writing exploits for win32 systems from scratch.
There are a few other exploit dev newbie questions i've seen a lot but i've never seen them answered: Creating your own simple exploit module for a remote code execution in web apps. Fuzzing is a very interesting research oriented area for.



![How to Write your Own Exploits [My 2 Cents] YouTube](https://i.ytimg.com/vi/XPDrwWRhAUQ/maxresdefault.jpg)